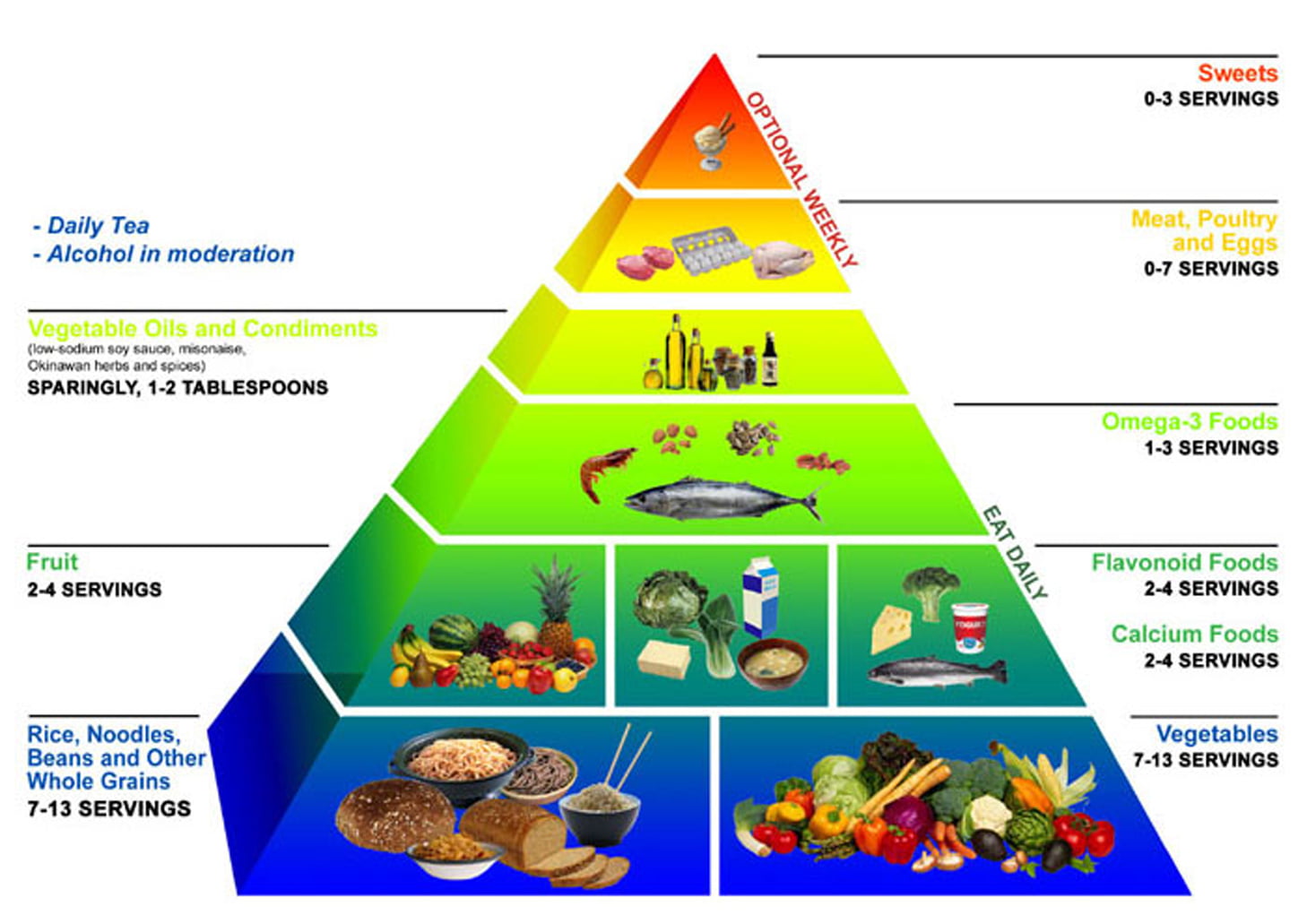
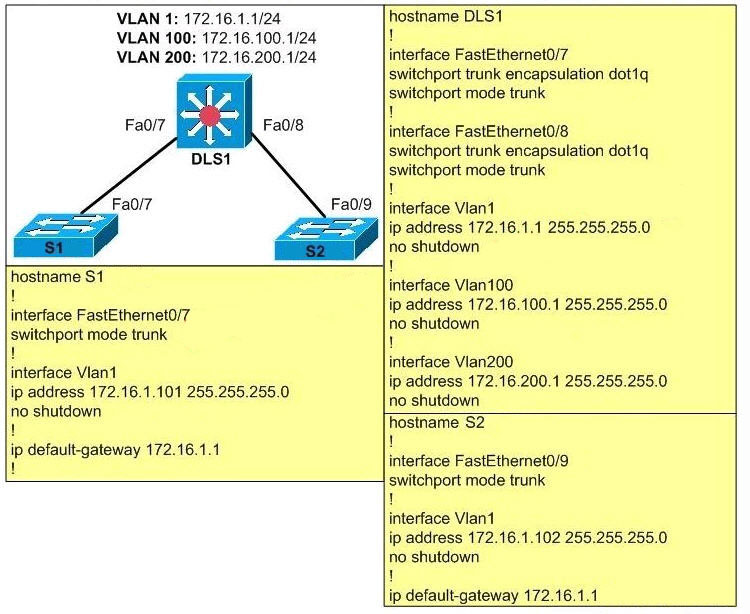
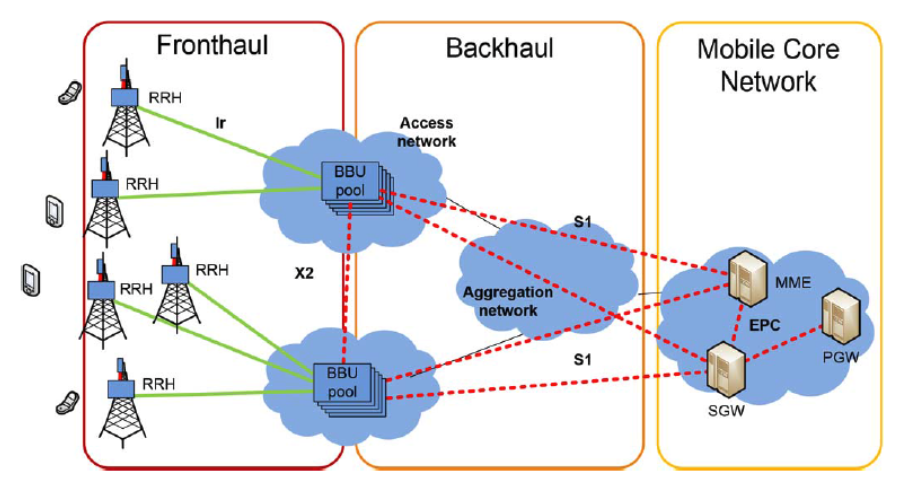
Cisco Confidential Network Layer Summary (cont. ) In addition to hierarchical addressing, the network layer is also responsible for routing. Hosts require a local routing table to ensure that packets are directed to the correct destination network. The local default route is the route to the default gateway. The default gateway is the IP address. The OSI model was designed to ensure different types of equipment (such as network adapters, hubs, and routers) would all be compatible even if built by different manufacturers. A product from one network equipment vendor that implements OSI Layer 2 functionality, for example, will be much more likely to interoperate with another vendor's OSI. Layer 2 and Layer 3 refer to different parts of IT network communications regarding layer networking and the standard for the OSI model. A network guru Tshirt from the 1980s shows Layer 8 as the financial layer, and Layer 9 as the political layer. The design was credited to Evi Nemeth. Contents Application Report SLLA270January 2008 Controller Area Network Physical Layer Requirements Steve Corrigan. ICP Industrial Interface ABSTRACT The multipoint bus structure and robust protocol of the HighSpeed Controller Area The entire LinkLayer Topology Discovery protocol is present in Windows 8. The Network Explorer Let's now take a look at the Network section of File Explorer. Expand your knowledge of the OSI network model with these useful facts that often get overlooked by beginners. Lifewire Common Questions and Answers on the OSI Network Model. Key Concepts Students learning networking often have difficulty memorizing the name of each layer of the OSI. I've recently discovered an extremely useful feature called Link Layer Topology Discovery in Windows 7 I click on See Full Map in the network and sharing center. How do I view the my network map in windows 8. How would I access the full network map from windows 8. 1 or later versions of windows. Network Security Network Layer Learn Network Security starting from Overview, Application Layer, Transport Layer, Network Layer, Data Link Layer, Access Control, Firewalls, Critical Necessity. identity as the 8th Layer or the human layer in the network protocol stack, enabling organizations to overcome the limitations of conventional UTMsfirewalls which bind security to IP addresses alone. By implementing Layer 8 security in their Cyberoam's Layer 8 Technology treats User Identity. Testout Networking Chapter 8, Network Pro, , . You want to maintain security on your internal network. OSI Layer 3 Circuitlevel Proxy OSI Layer 5 Applicationlevel Gateway OSI Layer 7 Routed Firewall OSI Layer 3 Transparent Firewall Chapter 4: Network Layer 4 1 I d i4. 2 Virtual circuit and dt t ks 4. 5 Routing algorithms Link state datagram networks Distance Vector 4. 3 Whats inside a router Hierarchical routing router 46 Routing in the 4. Welcome to the Layer 8 Network We are a collective of individuals to do cool stuff with tech. The OSI model for networking contains 7 layers to describe the architecture for data communications between computers connected via a network. While not an official layer of the OSI model, layer 8 is sometimes referred to as the user layer or political layer. Layer 8 is considered humorous in. Located at Layer 3 of the Open Systems Interconnection (OSI) communications model, the network layer's primary function is to move data into and through other networks. Network layer protocols accomplish this goal by packaging data with correct network address information, selecting the. Layer 3, the network layer of the OSI model, provides an endtoend logical addressing system so that a packet fere with the smooth design and operation of the network. Layer 8 is usually considered the office politics layer. In most organizations, there is at least one group who The Cisco 4Port and 8Port Layer 2 Gigabit EtherSwitch Network Interface Module (NIM) integrate the Layer 2 features and provides a 1Gbps connection to the multigigabit fabric (MGF) for. Layer 8 Definition The term layer 8 is a hypothetical layer that is used to analyze network problems and issues that are not covered by the View 8. pdf from COMP 3331 at University of New South Wales. COMP: Computer Networks and Applications Week 8 Network Layer. My classmate and group project partner, Chris O. is presenting the Network layer of the OSI Model. This can be helpful when learning networking fundamentals. Perintah Ipconfig Ipconfig adalahperintah command prompt yang yang. The third layer of the OSI Model, the network layer, is where most network engineers focus their time and expertise. As Darragh commented in my post on the data link layer, Layer 2 is cool but. videos Play all ccna network fundamentals Chapters 19 Sherzod Networking OSI Model PHYSICAL LAYER [ Fundamental Concepts Duration: 10: 09. ISO Training Institute 8, 682 views The Network Layer handles the task of routing network messages from one computer to another. The two most popular Layer3 protocols are IP (which is usually paired with TCP) and IPX (normally paired with SPX for use with Novell and Windows networks). When participating in the Layer 8political process, acknowledge ownership where it is due. This is a joint effort and there must be joint responsibility. Documentation is the key to not only hold people responsible but serves as a reminder of what is discussed, agreed upon and finally decided. Layer 10, the user layer, is in every organization. But users are much more than a layer. While they are one of the reasons the network exists, users. From Layer 5 application, Layer 4 transport layer, Layer 3, the internet layer, Layer 2, the network access layer, and Layer 1, the physical layer. The Network Access Layer and the OSI Model. As Hour 2, How TCPIP Works mentioned, TCPIP is officially independent of the sevenlayer OSI networking model, but the OSI model is often used as a general framework for understanding protocol systems. Shop eBay for great deals on Cisco 3 Layer 8 Port LAN Network Switches. You'll find new or used products in Cisco 3 Layer 8 Port LAN Network Switches on eBay. Free shipping on selected items. slices thickcut bacon, cut into 1inch pieces. One 16ounce can refried beans One 4ounce can diced green chiles 1 teaspoon ground cumin, plus more if needed Network layer 2 times and Data link layer 6 times. GATE CS 2013 Network Layer Discuss it. Question 1 Explanation: The network uses a Distance Vector Routing protocol. Once the routes have stabilized, the distance vectors at different nodes are as following. The OSI model explained: How to understand (and remember) the 7 layer network model while IP addresses work at Layer 3, the Network Layer. Main Task of the network layer is to move packets from the source host to the destination host Lowest layer to deal with end toend issues! Transport Session Presentation Application Transport Session Assume the capacity of the network links is 10 Mbs. 5G Network Architecture by ceyquem 2 February 2017 Here is a diagram that I found interesting, showing the logical architecture of a 5G network including the Core and Radio subsystems, as it is being discussed in the 3GPP working groups. Layer 8 Security is a cybersecurity consulting, advisory, and technical services company that creates risk management solutions for your evolving information security and compliance needs. Todays business environment requires seamless integration with thirdparty vendors, clients, and partners. SANS Institute InfoSec Reading Room This paper is from the SANS Institute Reading Room site. Reposting is not permitted without express written permission. Applying the OSI Seven Layer Network Model To Applying the OSI Seven Layer Network Model To Information Security By Damon Reed November 21, 2003 Network Layer Concerned with getting packets from source to destination. The network layer must know the topology of the Network Interface Figure 8. Networks: Routing 6 R R R R S S S s s s s s s s s s s R s R Backbone To internet or wide area network Organization Servers Gateway Departmental Server Storage network layer Two Cisco MDS switchesdirectors make up two separate fabrics to provide 16 Gb of FC connectivity between the compute and storage layer. The Cisco MDS model selection depends on the total number of SAN ports required to By definition, Cyberoam Layer 8 Technology over its network security appliances treat user identity the 8th layer or the human layer in the network protocol stack. This allows administrators to uniquely identify users, control Internet activity of these users in the network, and enable policysetting and reporting by username. The cloud is the next generation of business efficiency, security and savings and Layer 8 is your direct connection to it. Our highly experienced team works with you to design and deliver a complete range of cloud strategies, services and infrastructure that will help your business. How to choose the number of hidden layers and nodes in a feedforward neural network? up vote 403 down vote favorite. A rough approximation can be obtained by the geometric pyramid rule proposed by Masters (1993). For a three layer network with n input and m output neurons, the hidden layer would have \sqrtnm neurons. The third layer of the seven layers of Open Systems Interconnection (OSI) network model is the Network layer. The Network layer of the OSI model is responsible for managing logical addressing information in the packets and the delivery of those packets to the correct destination. The most significant protocol at layer 3 (also called the network layer) is the Internet Protocol, or IP. IP is the standard for routing packets across interconnected networkshence, the name internet. It is an encapsulating protocol similar to the way Ethernet is an encapsulating protocol. If we view the original check as a unit of data needed to be sent, we now have two envelopes required. The physical layer of the network focuses on hardware elements, such as cables, repeaters, and network interface cards. By far the most common protocol used at the physical layer is Ethernet. For example, an Ethernet network (such as 10BaseT or 100BaseTX) specifies the type of cables that can be used, the optimal topology (star vs. Layer 8 is written by Michael Cooney, an online news editor with Network World. Information technology Telecommunications and information exchange between systems Elements of management information relating to OSI Network Layer standards 95. 99 ISOIEC JTC 1SC 6 The network layer is the lowest one in the OSI model that is concerned with actually getting data from one computer to another even if it is on a remote network; in contrast, the data link layer only deals with devices that are local to each other. Schicht 3 Vermittlungsschicht (Network Layer) Die Vermittlungsschicht (engl. Da im Modell die letzte, siebte Schicht dem Benutzer am nchsten liegt, spricht man dann von einem Problem auf dem OSILayer 8, wenn dessen Ursache beim Benutzer selbst vermutet wird..