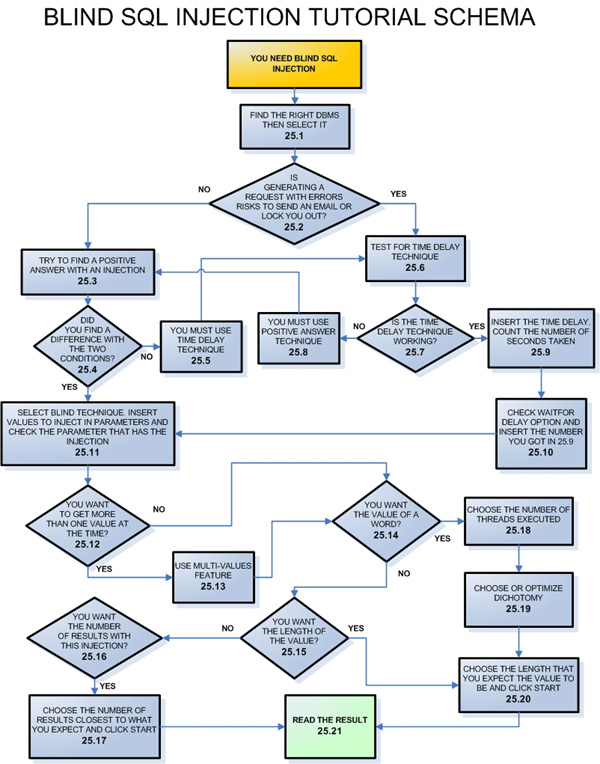
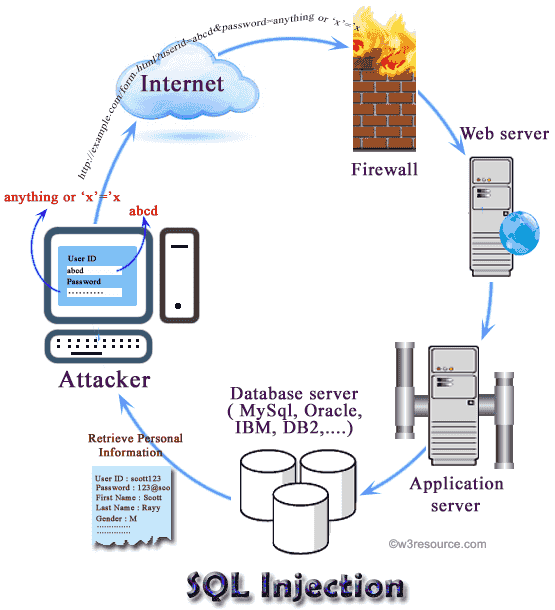
Common vulnerabilities SQL Injection Browser sends malicious input to server Bad input checking leads to malicious SQL query XSS Crosssite scripting SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and 3 Comments Manual SQL Injection Exploitation Step by Step Stanley September 12, 2017 at 12: 45 am Hello admin. please am trying to perform manual SQL on a site running on Apache 2. 2 please the example here starting with testphp is not working on the sites URL. and please I want to know if every manual SQL must have ARTISTS in url. sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. SQL Injection attacks are still as common today as they were ten years ago. Today I'll discuss what are SQLi and how you can exploit SQLi vulnerabilities fou SQL Injection Tutorial 1 What is SQL Injection SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not. This Tech Tip has not been intended to provide comprehensive coverage on SQL injection, or even a tutorial: it merely documents the process that evolved over several hours during a. SQL injection is Common and famous method of hacking at present. Using this method an unauthorized person can access the database of the website. Attacker can get all details from the Database. Ich habe mal ein Tutorial geschrieben, wie Angreifer eine SQL Injection durchfhren knnen. Das Tutorial soll nicht zu Straftaten anstiften und ich. This tutorial is about core principles of SQL injection. User supplied parameters frequently end up in the WHERE clause of dynamically built queries. The result Today I am gonna show you how to test for an SQL injection within a practice website with the Havij tool. SQL Injection is an attack type that exploits bad SQL statements SQL injection can be used to bypass login algorithms, retrieve, insert, and update and delete data. SQL injection tools include SQLMap, SQLPing, and SQLSmack, etc. SQL Injection is a malicious attack where malicious users can inject SQL commands (commonly referred to as malicious payload) in SQL statement that controls the web application database (commonly referred to as Relational Database Management System. SQL Injection attacks are still as common today as they were ten years ago. Today Ill discuss what are SQLi and how you can exploit SQLi vulnerabilities found in software. In this SQL Injection tutorial I will cover the following topics: What is SQL What does SQL do How SQL is used [ Pengertian SQL Injection SQL Injection merupakan sebuah teknik hacking dimana seorang penyerang dapat memasukkan perintahperinta What is SQL Injection. SQL injection refers to the act of someone inserting a MySQL statement to be run on your database without your knowledge. SQL injection is a technique (like other web attack mechanisms) to attack data driven applications. This attack can bypass a firewall and can affect a fully patched system. The attacker takes the advantage of poorly filtered or not correctly escaped characters embedded in SQL statements into parsing variable data from user input. we are on the right track now lets start the Blind SQL injection. Why we call it blind as we cant see anything we dont know anything what we do is just keep asking question from the database and get the reply in form of yes (Page loaded Normally) or NO (Page dint Loaded Normally). La inyeccin de SQL es una tcnica de inyeccin de cdigo que explota una vulnerabilidad de seguridad dentro de la capa de base de datos de una aplicacin. Esta vulnerabilidad puede encontrarse cuando la entrada del usuario se filtra de forma incorrecta debido a caracteres de escape embebidos en sentencias SQL. SQL Injection Tutorial by Marezzi (MySQL) In this tutorial i will describe how sql injection works and how to use it to get some useful information. The SQL injection has been in the headlines for years. But developers today can use Source Code Analysis (SCA) to eliminate the SQLi vulnerability. Blind SQL injection is nearly identical to normal SQL Injection, the only difference being the way the data is retrieved from the database. When the database does not output data to the web page, an attacker is forced to steal data by asking the database a series of true or false questions. One particularly pervasive method of attack is called SQL injection. Using this method, a hacker can pass string input to an application with the hope of gaining unauthorized access to a database. By taking this selfstudy tutorial, you can arm yourself with techniques and tools to strengthen your code and applications against these attacks. Both SQL and NoSQL databases are vulnerable to injection attack. Here is an example of equivalent attack in both cases, where attacker manages to retrieve admin user's record without knowing password. SQL is a database computer language designed for the retrieval and management of data in a relational database. SQL stands for Structured Query Language. This tutorial will give you a quick start to SQL. It covers most of the topics required for a basic understanding of SQL and to get a feel of how. SQL injection is a code injection technique, used to attack datadriven applications, in which nefarious SQL statements are inserted into an entry field for execution. A complete reference about SQL injection. Introduction, tutorial, advanced attack techniques, how to avoid it, resources and much more. SQL Injection is a type of attack that allows the attacker to extract database information from the websites SQL database. What is SQLMap SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws. Post your valuable post about any necessary software with crack. and give some little description about How to use and why its necessary. SQL Injection is a code injection technique. It is the placement of malicious code in SQL strings. SQL Injection is one of the most common web hacking techniques. Hacking a website isnt difficult. In fact, in this SQL injection tutorial, you learn how easy it really is to become a proficient website hacker using SQL injection techniques. 1 PHP MySQLi Prepared Statements Tutorial to Prevent SQL Injection Nov 8, 2017 2 PHP PDO Prepared Statements Tutorial to Prevent SQL Injection Nov 26, 2017 3 PDO vs. MySQLi: The Battle of PHP Database APIs Jun 8, 2018. Firmly believes that web technologies should take over everything. Enjoys writing tutorials about. SQL Injection can be broken up into 3 classes Inband data is extracted using the same channel that is used to inject the SQL code. This is the most straightforward kind of. Sqlmap is the most popular tool for carrying out automated sql injections against vulnerable systems. In this tutorial we are going to learn to use it. If you take a user input through a webpage and insert it into a SQL database, there is a chance that you have left yourself wide open for a security issue known as the SQL Injection. This chapter will teach you how to help prevent this from happening and help you secure your scripts and SQL. Clique aqui para ver o nosso novo site Criei este tutorial a fim de demonstrar uma das melhores formas de invaso e uma das mais usadas hoje em dia. Ate porque os programadores de hoje em dia no esto si importando com a segurana do site e suas reas restritas. OBS: no vou explicar aqui Il tutorial sull'attacco SQL injection presenta brevemente una delle minacce pi comuni alla sicurezza sul Web per le aziende e le organizzazioni pubbliche. This SQL injection tutorial provides a brief introduction to one of the most common threats to web security for businesses and public organizations. SQL Injection Many web developers are unaware of how SQL queries can be tampered with, and assume that an SQL query is a trusted command. It means that SQL queries are able to circumvent access controls, thereby bypassing standard authentication and authorization checks, and sometimes SQL queries even may allow access to host operating system. Follow this SQL Injection Tutorial to develop an understanding of what SQL Injection is and how it works. SQL Injection breaches are a regular occurrence. How to exploit the SQL Injection Attack. Exploiting an SQL Inject attack involves solving a puzzle that is a cross between Hangman and 20 Questions. That being said, blind SQLi involves a lot of guessing, and the fact that I can use union based sql injection (classical injection that we did already) to find out table names, etc. makes it much easier for me to write the tutorial. [SQL Injection Help Desk I Will Do My Best To Help You [SQL Injection Help Desk. SQL is a standard language for storing, manipulating and retrieving data in databases. Our SQL tutorial will teach you how to use SQL in: MySQL, SQL Server, MS Access, Oracle, Sybase, Informix, Postgres, and other database systems. Read our SQL injection cheat sheet to learn everything you need to know about sql injection, including key concepts, examples and tips. SQL injection is an attack wherein an attacker can inject or execute malicious SQL code via the input data from the browser to the application server, such as webform input. It can be used to expose sensitive information like user's contact numbers, email addresses, credit card information and so. In this tutorial ill show you how sql injection works and how to use it to extract information from the database. The UNION operator is used in SQL injections to join a query, purposely forged by the tester, to the original query. SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input. SQL injection usually occurs when you ask a user for input, like their. Just how bad is it if your site is vulnerable to an SQL Injection? Dr Mike Pound shows us how they work. Cookie Stealing: Rob Mi SQL Injection is still the biggest security problem in web applications. This year we can celebrate it's the 10th anniversary of SQL Injection. Even if the problem is know since 10 years the knowledge especially for exploiting Oracle databases is poor..